Joseph Lau is the Chief Information Security Officer at Portage Ventures.

Congratulations, you’re now a growth company! After countless 70+ hour work weeks, bottomless coffees, and sleepless nights wondering if your startup would survive, you’ve earned loyal customers and investors who believe in you, and some runway to fuel growth.
But… I think it’s time we had “The Talk.” You’re not a little seed-stage startup anymore.
You were under the radar as a Series A company, but recently you’ve been in the news a lot. TechCrunch and Forbes both had some flattering things to say about your rapid growth. But aside from potential customers and investors, you know who’s also reading those articles?
Malicious cybercriminals and fraudsters.
That same positive spotlight has also attracted negative attention from hackers, and they’re starting to aggressively probe your Cloud SAAS platform. You’ve probably heard that Colonial Pipeline just paid a $4.4 million ransom to hackers after ransomware shut down their East Coast operations. In late March, insurer CNA Financial paid $40 million to hackers that shut down their network. Unfortunately, there’s no better encouragement for cybercriminals to develop even more sophisticated hacking tools. In fact, US Fed Chairman Jerome Powell recently said that the biggest risk for the financial sector is now cyber risk. What does all this mean for you?
Basic cybersecurity protections are not enough.
In my post on the Startup 7, I explained seven cybersecurity pillars for early-stage startups. Working with the awesome security teams at Dialogue (our first portfolio company to IPO) and Wealthsimple (which recently closed a large round of fundraising), we’ve developed the “Growth Stage 11.” The Growth Stage 11 builds on the foundation of your existing Startup 7 cybersecurity program and gets you ready as you enter the next chapter of your journey. In this post, I’ll break down the four additional security pillars to help your organization improve its overall cybersecurity maturity.
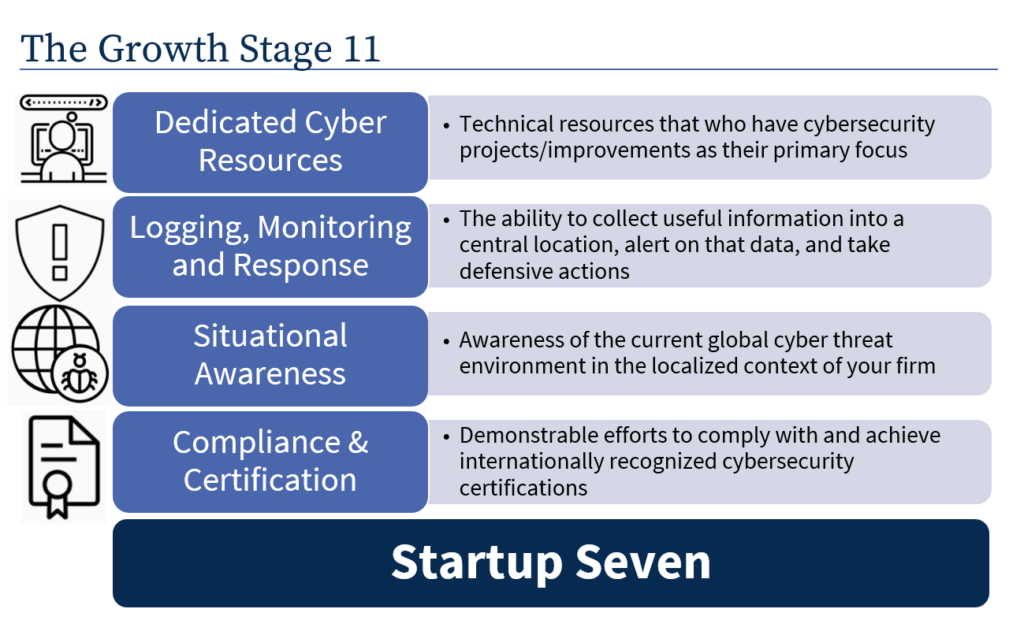
#1 Dedicated Cyber Resources
If you suffer a cyber attack, do you have someone on the ground ready to respond? Up to this point, you’ve probably been able to manage cybersecurity as one of the dozens of engineering teams’ tasks. But once you hit 100 employees or so, it’s time to invest in full-time resources focused on cybersecurity as their primary responsibility. When something happens, you need someone able to respond immediately. Unnecessary delays can be disastrous.
Your first cybersecurity leader is critical to the success of your cybersecurity program, as they will help set the strategy and direction. Beyond their cyber skills, this person needs to be an excellent communicator that can build and manage a team, train new people, and get the rest of the company on board. My colleague Alex Manea at Georgian has some really good insights on how to hire your first cybersecurity leader here. My advice? Start looking early, because it’s likely to be a long hiring process.
It’s also a good idea to outsource certain functions to managed security service providers because you can’t do everything yourself — especially 24/7 coverage. But keep in mind that strategic decisions should always be made internally.
#2 Logging, Monitoring, and Response
You can’t prevent threats if you don’t know about them. As the company scales, collecting security logs and actually monitoring those logs are crucial to anticipating and blocking cyber threats.
But please, please, please, do NOT collect everything. Collecting everything is not a strategy. It creates a heavy burden because all that data is impossible to sift through. Logging is not about collecting everything; it’s about collecting the right things. What to log and how to do it is highly specific to each organization, but here’s a starting point from OWASP. Be selective about what you collect, then centralize the logs in one location in an accessible format, so you have the capability to search. If it takes you a week to search your repository, it’s useless.
Once a system for logging is in place, the cybersecurity team should monitor it regularly. But almost immediately, you’ll probably notice a problem. There’s simply too much data for humans to analyze! You’ll never have a big enough team. To avoid drowning in alerts, move your monitoring towards automation. In an ideal world, your system will detect, flag, and respond to threats on its own, in real-time. That may seem like a pipe dream right now! But keep moving toward it.
#3 Situational Awareness
Cyber threats evolve at the pace of the Internet. And no one can predict what the Internet will look like a year from now. Just fifteen months ago, nobody thought that most office employees could work from home long-term. And yet, that’s what we’ve been doing since March 2020. Since rapid change is the new normal, it’s critical to stay vigilant about current events and how they might apply to your company. And not only stay vigilant — but also take immediate action! If you receive a notification that there is a major Microsoft vulnerability being actively exploited and there’s a patch available, do you have the ability to quickly patch your servers and workstations?
Cybersecurity is a team sport. Learn from others, and proactively use that information to defend yourself and your neighbors. Think about it this way: if you see that cars on a certain street are getting their windows smashed, don’t park on that street. And be a good neighbor by letting other people know not to do so as well.
Keep in mind that not all attacks are against your IT network. Cybercriminals will also impersonate members of your executive team or your brand on social media. Others will “squat” on lookalike domains, or push doctored versions of your mobile app into unauthorized app stores. While these attacks might seem trivial compared to ransomware, remember that the finance sector is built on trust. Your brand is your most valuable asset!
#4 Compliance & Certification
To be honest, I am not a huge fan of cybersecurity certifications. I feel they can foster a false sense of security. But once you’ve passed the seed stage, certifications like ISO 27001 and SOC 2 Type II are a necessary hoop to jump through. They are a sales tool that can enable partnerships with larger companies, and — if you’re lucky — they’ll allow you to skip doing those 200–300 question cybersecurity forms that some of those larger organizations ask for.
But just to be crystal clear: having these certifications doesn’t mean you’re secure! All the large corporations that were recently hacked had all the “best” certifications. Certifications alone aren’t enough.
Perhaps more important than the certifications themselves is the spirit of certification: due diligence on yourself and potential partners. In addition to the technical aspects, make sure you are doing background checks on new hires and due diligence on your critical third-party vendors. Your data is only as safe as who has access to it and where it’s stored. If you’re handing it over to a third party, you’ll want to fully understand and accept the risk involved.
In Conclusion
I realize the Growth Stage 11 is a lot more homework. But that’s all part of putting on the big kid shoes as you go out and change the world for the better! If properly implemented, your cybersecurity strength will even become a competitive advantage to set you apart from the competition. In fact, you may even be able to get a good night’s sleep if you skip the after-dinner espresso, while on a well-deserved vacation (when we can safely travel again). Now wouldn’t that be nice?


